
Cyber Security Policy and Management
1. Cyber Security Risk Management Structure
The Company has established the Information Security Management Committee as the highest authority for overseeing information security.
Chaired by the President, the committee is responsible for strategic decision-making, reviewing, and resolving critical in-formation security matters. To ensure effective execution, an Information Security Officer, reporting to the President’s Office, provides dedicated support to the committee’s activities and initiatives.
The IT Division acts as the operational unit for implementing information security measures. In alignment with the Company’s information security policies and guidelines, it establishes and maintains robust measures to effectively prevent and mitigate information security risks.
The Audit Office serves as the supervisory unit for information security. It conducts regular audits, and if any deficiencies are identified, the audited unit is required to promptly submit improvement plans to the Board of Directors. The Audit Office also monitors the progress of these improvements to reduce internal information security risks.
Additionally, certified public accountants (CPAs) perform annual audits of the Company’s information operations. Any deficiencies identified are addressed through corrective measures, with follow-ups to ensure proper implementation.
Recognizing the critical importance of information security, responsible units provide regular updates to the Board of Directors on the Company’s information security governance and implementation status. The most recent report was presented on December 12, 2024.
2. Cyber security Policy and Management Program
To strengthen the cyber security management and ensure the availability, integrity, and confidentiality of information, as well as to protect it from intentional or accidental threats from internal and external sources, the Company’s cyber security facilities and management practices are categorized into six major items:
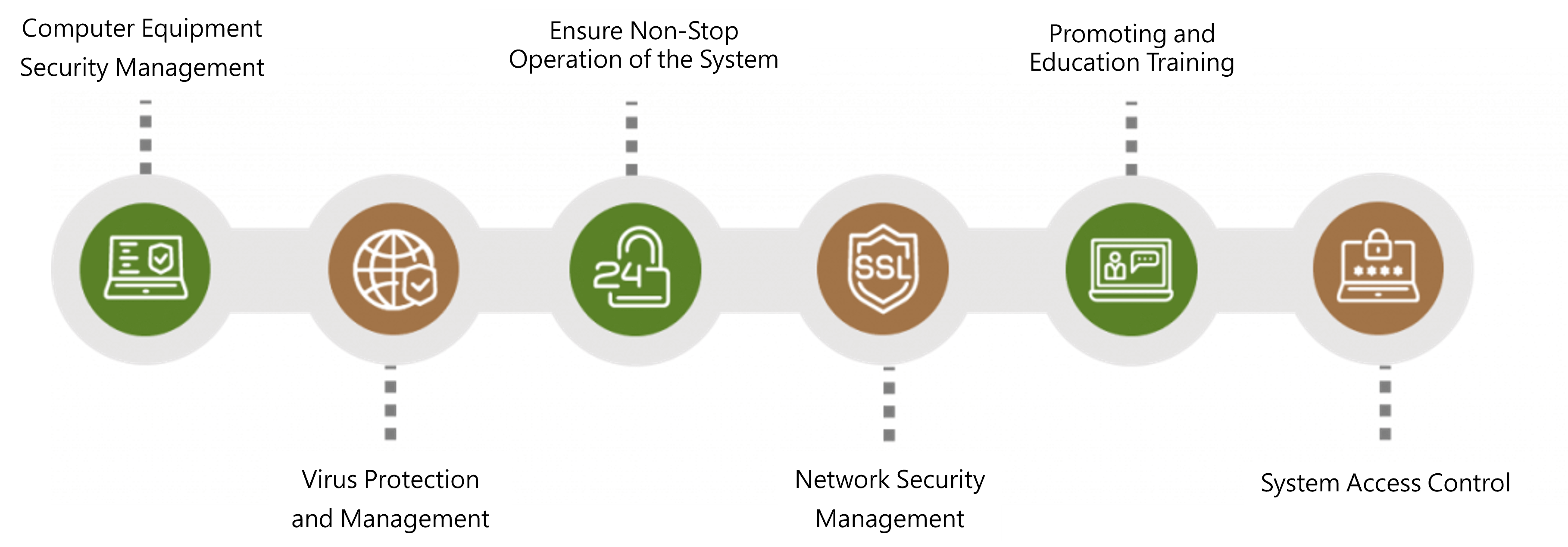
3. Commitment of resources to cyber security management
To fulfill the six major cyber security policies, the resources invested are as follows:
(1) Network hardware equipment such as firewalls, email anti-virus, spam filtering, Internet behavior analysis, and network management hubs.
(2) Software systems such as endpoint protection systems, backup management software, VPN authentication and encryption software.
(3) Telecommunication services such as multiple lines, cloud backup service, intrusion protection service, etc.
(4) Investment in manpower such as: daily system status check, weekly regular backup and backup media off-site storage implementation, at least two times a year cyber security publicity and education courses, annual system disaster recovery exercise, annual internal audit of the information cycle, accountant audit, etc.,
(5) Cyber security manpower: A dedicated cyber security head and a dedicated cyber security officer are responsible for cyber security structure design, cyber security maintenance and monitoring, cyber security incident response and investigation, and review and revision of cyber security policies; the dedicated cyber security officer reports to the board of directors at least once a year.
4. Losses and Measures for Significant Security Incidents in Recent Years
From January 2024 to December 2024, there were no significant security incidents.
5. Cyber Security escalation Procedure
In the event of a computer system abnormality, personnel should immediately notify the IT division for handling. IT personnel should be aware of cyber security when dealing with computer system abnormality or troubleshooting, and the following situations should be reported to the head of IT division, and those that are categorized as cyber security incident should be notified to the Executive Secretary of the Crisis Management Team (EST) in accordance with crisis management procedures to assess whether it is a major cyber security incident.
(1) The external network is interrupted for 30 minutes and cannot be restored.
(2) An information system anomaly has occurred and has not been restored after 3 hours.
(3) The number of computers infected by computer viruses is found to be more than 3% of the total number of computers.
(4) Signs of hacking, or system data being tampered with or exfiltrated for no reason are found.
6. Cyber Security Awareness
The Company conducts social engineering drills every year to raise employees’ awareness of cyber security. The latest social engineering drill was held on November 13, 2024, and employees who have not passed the social engineering drill have to go through compulsory training session.

